Introduction to lsof on macOS
The lsof command, which stands for “list open files,” is one of the most powerful diagnostic tools available on macOS systems. Compatible with the latest macOS 15.5 Sequoia and all previous versions, this command provides comprehensive insights into file system activity, network connections, and process behavior. Whether you’re troubleshooting port conflicts, investigating security issues, or optimizing system performance, mastering lsof is essential for any macOS administrator or power user.
In macOS, everything is treated as a file – regular files, directories, network sockets, devices, and pipes. This fundamental principle makes lsof incredibly versatile, allowing you to monitor virtually every aspect of your system’s resource usage. This comprehensive guide covers the most practical lsof commands and scenarios you’ll encounter in real-world macOS environments.
Understanding lsof Output Format
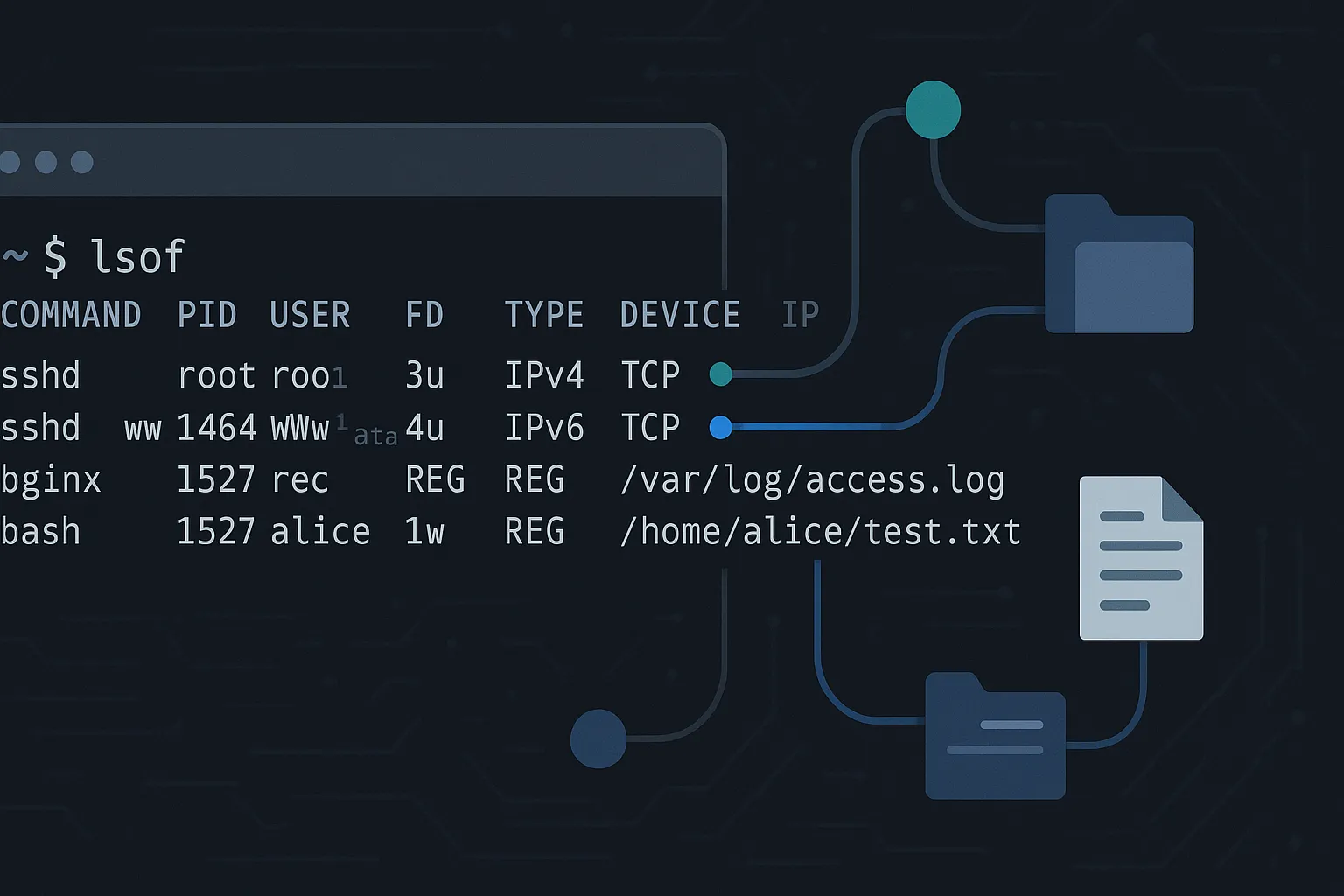
Before diving into specific commands, it’s crucial to understand the lsof output format. The standard output contains several columns:
- COMMAND: The name of the process that opened the file
- PID: Process ID of the command
- USER: Username or user ID of the process owner
- FD: File descriptor and access mode (r=read, w=write, u=read/write)
- TYPE: File type (REG=regular file, DIR=directory, IPv4=network socket)
- DEVICE: Device numbers or network protocol
- SIZE/OFF: File size or offset
- NODE: Inode number or protocol-specific information
- NAME: File name or network connection details
Essential lsof Commands for macOS
Basic File System Monitoring
List all open files on your system (warning: this produces extensive output):
lsofTo make the output more manageable, pipe it through less:
lsof | lessFind which processes are using a specific file:
lsof /path/to/specific/file.txtList all files opened in a specific directory:
lsof +D /Users/username/DocumentsProcess-Based File Monitoring
Show all files opened by a specific process ID:
lsof -p 1234Display files opened by processes whose command names start with specific characters:
lsof -c Chrome
lsof -c /^node/List files opened by a specific user:
lsof -u usernameExclude files opened by root user:
lsof -u ^rootNetwork Connection Monitoring
Port and Network Analysis
One of lsof’s most valuable features is network monitoring. Show all network connections:
lsof -iFind which process is using a specific port (essential for troubleshooting port conflicts):
lsof -i :8080
lsof -i TCP:3000
lsof -i UDP:53Show connections to a specific host:
lsof -i @192.168.1.1List all TCP connections in LISTEN state:
lsof -i TCP -s TCP:LISTENDisplay IPv4 connections only:
lsof -i 4Advanced Network Filtering
Show connections within a port range:
lsof -i TCP:1024-65535Monitor specific network protocols:
lsof -i TCP
lsof -i UDPReal-World Troubleshooting Scenarios
Unmounting Disk Issues
When macOS won’t let you eject an external drive, use lsof to find which processes are accessing it:
sudo lsof "/Volumes/External Drive Name"This reveals processes keeping the volume busy, allowing you to safely terminate them before ejecting.
Port Conflict Resolution
If a development server fails to start due to a port being “already in use,” identify the culprit:
lsof -i :3000Then kill the process if necessary:
kill -9 $(lsof -ti:3000)Process Analysis for Performance
Monitor file access patterns for a specific application:
sudo lsof -c "Application Name" -r 2The -r 2 flag refreshes the output every 2 seconds, providing real-time monitoring.
Advanced lsof Techniques
Combining Multiple Conditions
Use logical operators to create complex queries. Find files opened by a specific user on a particular port:
lsof -u username -i :8080Show deleted files still held open by processes (useful for disk space analysis):
lsof | grep deletedOutput Formatting Options
For script-friendly output, use the terse format:
lsof -t -i :80This returns only PIDs, perfect for automated process management.
Generate parseable output for other programs:
lsof -F pcutnSecurity and Monitoring Applications
Monitor suspicious network activity:
sudo lsof -i -n -P | grep ESTABLISHEDThe -n flag prevents hostname resolution (faster), and -P shows port numbers instead of service names.
Track file access in sensitive directories:
sudo lsof +D /private/var/logmacOS-Specific Considerations
Permission Requirements
On macOS, lsof typically requires elevated privileges to show processes from other users. Use sudo for comprehensive system-wide monitoring:
sudo lsofWithout sudo, lsof only displays your own processes, which may be sufficient for many troubleshooting scenarios.
System Integrity Protection (SIP)
macOS System Integrity Protection may limit lsof’s ability to inspect certain system processes. This is normal behavior and doesn’t indicate a problem with the command.
Performance Considerations
On busy macOS systems, lsof can be resource-intensive. Use the -b flag to avoid kernel blocking operations:
lsof -bPractical Examples for Developers
Web Development Scenarios
Check if your development server is running:
lsof -i :3000 -i :8080 -i :8000Monitor database connections:
lsof -i :5432 -i :3306 -i :27017Docker and Container Monitoring
Find Docker containers accessing specific ports:
lsof -i | grep dockerMonitor container file system access:
sudo lsof -c dockerAutomation and Scripting
Creating Monitoring Scripts
Here’s a simple script to monitor port usage:
#!/bin/bash
# Monitor specific ports and alert if in use
PORTS="3000 8080 9000"
for port in $PORTS; do
if lsof -i :$port > /dev/null 2>&1; then
echo "Port $port is in use by:"
lsof -i :$port
fi
doneIntegration with Other Tools
Combine lsof with other Unix tools for powerful system analysis:
# Count open files by process
lsof | cut -d' ' -f1 | sort | uniq -c | sort -nr
# Find processes with the most network connections
lsof -i | grep ESTABLISHED | cut -d' ' -f1 | sort | uniq -c | sort -nrCommon Issues and Solutions
Permission Denied Errors
If you encounter “Permission denied” errors, ensure you’re using sudo for system-wide monitoring. Some processes may still be protected by macOS security features.
No Output or Incomplete Results
If lsof returns no results when you expect output:
- Verify the file or port actually exists
- Use sudo for comprehensive results
- Check if the process has already terminated
- Ensure correct syntax (spaces matter in lsof commands)
Performance Issues
If lsof runs slowly on your system:
- Use the
-bflag to avoid blocking operations - Specify exact targets instead of broad queries
- Use
-nand-Pflags to avoid DNS lookups
Best Practices and Tips
Efficient Usage Patterns
- Start with specific queries rather than broad searches
- Use appropriate flags to limit output scope
- Combine lsof with grep for targeted filtering
- Save complex queries as shell aliases or functions
Security Considerations
- Be cautious when killing processes identified by lsof
- Verify process legitimacy before termination
- Use lsof for monitoring but not as a primary security tool
- Regular monitoring can help identify unusual system behavior
Conclusion
The lsof command is an indispensable tool for macOS system administration, development, and troubleshooting. From resolving port conflicts to investigating security issues, understanding lsof’s capabilities will significantly enhance your ability to manage macOS systems effectively. Whether you’re running the latest macOS 15.5 Sequoia or an earlier version, these commands and techniques remain essential for any serious macOS user.
Remember that lsof’s true power lies not just in individual commands, but in combining them creatively to solve specific problems. Practice these examples in your own environment, and don’t hesitate to explore the comprehensive manual page with man lsof for even more advanced options and use cases.
As macOS continues to evolve, lsof remains a reliable constant in the system administrator’s toolkit, providing deep insights into system behavior that GUI tools simply cannot match. Master these techniques, and you’ll be well-equipped to handle virtually any file system or network-related challenge on macOS.